|
|
PGTS Humble BlogThread: Internet Security/Malware/Spam |
|
 |
Gerry Patterson. The world's most humble blogger |
| Edited and endorsed by PGTS, Home of the world's most humble blogger | |
| | |
Peak Spam |
|
Chronogical Blog Entries: |
|
| | |
Date: Wed, 25 May 2011 23:57:34 +1000In July 2002, I composed an online article titled "Reducing Spam Rage". This was followed by a series of articles on spam, two of the most well-known being "A Few Inches More Please" and "Spam Turkey Bastards". I also engaged in some investigations into spam, which with the benefit of hindsight, I probably would not have done, because my email inbox was subsequently subjected to a frightening torrent of spam. Subsequently, this has necessitated the construction of an array of defences against this modern day pestilence. Over the years various counter-measures have effectively combated it ... But the volume of attempted spam attacks rose inexorably ... Until recently, when inbound spam almost ceased ... Something had changed! ... Although it may not have been a change for the better. |
|
It seems that cyber-crime is becoming a well organised and sophisticated global activity. And spam is becoming well constructed and most worrying of all it may now be targeted.
For the PGTS domain the quantities of email blocked by or reported to spam assassin is as follows:
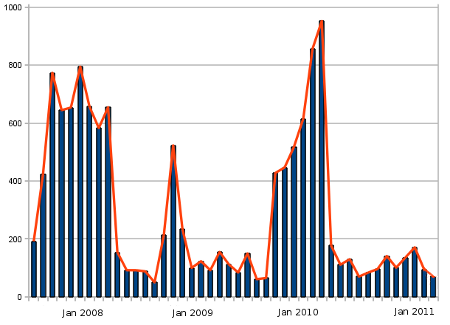
Spam (assassinated) Stats PGTS Domain.
The figures for May 2011, have been estimated by using three week's worth of data and multiplying by 1.33.
For other domains which are hosted by PGTS there is less integration between the MUA and the firewall. This is because email is routed to remote workstations to be read by third parties. Before being forward it is scanned by spam assassin and high scoring headers are kept for investigation. The quantities of email blocked by or reported to spam assassin is as follows:
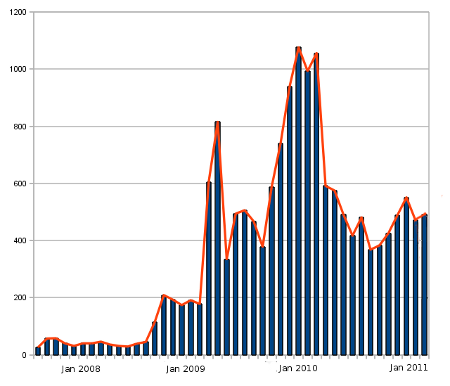
Spam (assassinated) Stats non-PGTS Domains.
In my own domain, there are three levels of defence against SPAM:
-
RTBL (Real Time Black List). This is applied by the MTA (Mail Transport Agent).
-
Spam Assassin. This is an open source perl, content-based filter, which is combined with procmail, an intermediate layer between the MTA and the MUA (Mail User Agent).
-
A suite of perl scripts which record IP addresses and integrate the RTBL, spam assassin and access blacklists for the MUA, MTA and firewall.
Unfortunately I have not been able to compose figures for inbound mail blocked by the MTA using RTBL. This would give a much better estimate of the total amount of spam. Since the amount of email blocked using RTBL is typically 5 to 10 times greater than the amount stopped by spam assassin and because I am not able to see the content (it is rejected during the negotiation phase), the only data available are the "To and purported From data. There will be a script to log and analyse spam blocked using RTBL ... It is definitely on my TODO list ... But for the time being I don't have any accurate statistics from the MTA logs.
Nevertheless the graphs above do tell an interesting story. Spam assassin is deployed after emails have negotiated their way past the firewall. By including a policy RTBL in the black lists, the firewall will reject much of the spam delivered by zombies and client workstations that are not "supposed" to be sending email --- A policy RTBL will reject mail from known dynamic address ranges, since many ISPs publish their IP address ranges. The only problem with policy RTBLs is that they can be out of date.
It seems that spam intercepted by spam assassin peaked in March 2010. It also seems that the counter-measures for email addresses in the PGTS domain are proving effective.
And since about April 2011, the incidence of spam in the PGTS domain has almost fallen off a cliff. This is true for spam intercepted by spam assassin and spam blocked by RTBL.
Spam for non-PGTS domains also seems to have peaked.
The marked difference in the quantities for PGTS and non-PGTS suggest that there is feed-back in the overall spam production/delivery cycle. In other words spammers are checking logs and doing some (possibly crude) profiling for victim domains and/or IP addresses.
However, although these figures indicate a "spam peak", the type of spam has changed considerably. Most BUCE (Bulk Unsolicited Commercial Email) is now sent from genuine servers with genuine remove options ... Although after you request to be removed you may be put onto another list (without being consulted).
On the other hand, spam that is sent with forged headers, these days, is most likely to be part of a phishing scam. And the overall quality of all spam is much improved. There are less spelling and grammar errors. And the phishing emails have been cleverly constructed to entice users to install malware.
Several of the recent samples of spam that I have examined have been better constructed then those from the earlier noughties decade. Spam is still mainly targeted at Microsoft Outlook, however there are signs that spammers are learning to diversify. Some of them are thinking about targeting Mac OS X as well as Microsoft. However most of the attempts are half-hearted and often rely on Crossover for Mac rather than a native Mac vulnerability.
To date no-one seems to given serious consideration to targeting Linux.
Another interesting development is the fact that Firefox, Chrome and Google seem to be constructing lists of malevolent websites. If a website contains code that is connected with phishing scams or other fraudulent activities, there will often be a warning concerning the site. Bing seems to be much slower at picking these up. I cannot run MSIE, so I am unable to comment on the safety provisions in IE8.
Trusteer Rapport Malware
An example of the new sophisticated malware is the so called "Trusteer Rapport" scam. A recent example which I analysed used an HTML email to deliver a binary payload intended for Microsoft PCs. It it seems to have been tailored for Microsoft Outlook and Internet Explorer, although it will probably infect any Microsoft computer. A recent sample of this malware which arrived at my mailhub was as follows:
Headers:
HTML Text:Trusteer Rapport adds valuable security when you log on to Westpac Internet Banking. It checks that you are using the real Westpac website and not a fake. It locks down the link between you and the bank so that fraudsters can't listen in. Finally, it blocks all known viruses that target online banking. Rapport doesn't replace your Personal Internet Banking security details or other protection such as anti-virus software. It works with them to add extra security. It only takes a few minutes to install the software and there is no need to restart your computer. |
Note: Real email addresses have been struck-out.
The binary payload was called westpac.exe and was 715264 bytes in size: GNU checksum reported as follows:
4005364463 715264 westpac.exe
The text was rendered with fonts and backgrounds that resembled text formatted by the Westpac bank and there was a Westpac logo in the corner (served up by www.hscco.com.au). There was also several links to a numeric IP address 124.9.47.194, which offered a windows .exe payload. The package seems to have been manufactured in China.
There is an organisation known as Trusteer which offers software which will "protect" your computer from viruses. You can find their official website at www.trusteer.com.
What the Trusteer website instructs you to do is wait until your bank offers you a copy of Trusteer Rapport as part of their security policy. There is a list of banks who (they claim) recommend the product. They also ask you for your name and email address in case your bank is not mentioned in the list of supported banks. There are no details of what the product actually does. The only installation instructions show someone clicking on a link in Windows XP. The link is to an online .exe file. The person then clicks "OK" a few times and there you are! <sarcasm> Completely safe from malware! </sarcasm>
With such a poor security model and a website designed for push marketing, it is little wonder that these scammers have piggy-backed onto the Trusteer distribution model. After all, the email purports to be from your bank. And if you were running XP and clicked on the button in the email ... An executable file would be downloaded and there you are! <sarcasm> Completely safe from malware! </sarcasm>
Except of course, sarcasm aside. There is little safety for users who don't understand the difference between a browser and an MUA ... And since most software designers are busily doing their level best to disguise such differences there is little chance that the public will keep up with the latest phishing scams such as the above, which are well-engineered and targeted.
There must be many victims ... Otherwise the scammers wouldn't bother!
iFrame Malware
A nasty password harvesting scam which bedevils webmasters is known as iFrame malware. Brian Robson, who hosts the Bondi website, relates here how his statistics changed when his password was harvested and his index pages were hacked with the iFrame exploit. The iFrame hack targets Microsoft clients. However since most web servers are Apache on Linux, this malware specialises in attacking Apache hosts via the FTP interface on the compromised client. Sadly, many websites are maintained from Microsoft clients using FTP of some form or another ... The iFrame malware harvests FTP passwords ... It also looks for index.html, index.shtml and index.php. Whenever the victim tries to transfer these files to the server they are hacked with the iFrame code.
Once the hacked pages have been uploaded, it helps spread the malware ... If another unsuspecting webmaster (using a Microsoft machine) views one of the hacked pages, the malware leapfrogs into another workstation and starts searching for FTP passwords. Apparently this malware can also be sent via email.
As Brian relates, a hacked website very quickly loses its page rank in Google, but regains it once it has been fixed (although not quite as quickly). Bing and Yahoo however do not do this ... After all, Although Microsoft seems to pay little regard to the welfare of their unfortunate users, they do often remind us that security is the responsibility of individual users. So far they haven't got the message ... They are still using Microsoft products.
BUCE from 68.233.235.190
As the failure of anti-spamming legislation becomes increasingly difficult to refute, some organisations are attempting to build businesses that appear legitimate using BUCE (Bulk Unsolicited Commercial Email). A recent example was the host at 68.233.235.190,
This IP address does not have a DNS entry. At present it is registered as belonging to Henry Silva in Peru, although the IP address seems to have been allocated to the USA. I first noticed email from this address in 2007. It was mainly "link-building" BUCE, sent to one of the non-PGTS domains. It was soon marked up by spam assassin There were only five emails in the first lot of BUCE in 2007. Then there was a long silence until early 2011, when spam assassin began diverting email from 68.233.235.190. Once again the emails were mostly link building BUCE ... The same four email address that had been used earlier appeared again except that "Amber Huber" had changed her name to "Amber Patel" ... And there many other additional email addresses.
All the emails were sent to just two address that were not in the PGTS domain. Now, it might have been possible that these were obtained because those two addresses had subscribed to a webmaster forum. However amongst all the offerings of "promotions" and weblinks there were two instance of employment SPAM which had been sent using the fake bounce message technique (backscatter), which consists of a delivery failure notification sent from a server, either by persuading it that an email has failed (by sending a message to a bad address with forged recipient and/or reply-to tags), or by forging a bounce request and passing it along to the target. The bounce notification contains the payload as an attachment.
And of course, fake bounce messages are never employed by a legitimate online business.
These are the statistics of the (purported) email addresses sent from 68.233.235.190 and intercepted by spam assassin (most of them in 2011):
| Email Address | Num |
| rhianne.macpherson@gmail.com | 126 |
| sandy.keiths@gmail.com | 111 |
| sylvie.brinkley@gmail.com | 94 |
| knight.lily876@gmail.com | 92 |
| melissa.green.a@gmail.com | 84 |
| heather.klum@gmail.com | 52 |
| loren.krips@gmail.com | 47 |
| lily.holmes14@googlemail.com | 46 |
| brigitte.crawford@gmail.com | 41 |
| rebekka.alt@gmail.com | 40 |
| kim.martins.a@gmail.com | 34 |
| leah.shaw23@gmail.com | 31 |
| phoebe.marshall333@googlemail.com | 30 |
| ruby.cooper47@gmail.com | 28 |
| kristin.berry.a@gmail.com | 27 |
| mary.brown.b@gmail.com | 27 |
| estelle.anderson.e@gmail.com | 23 |
| molly.jackson.a@gmail.com | 18 |
| monica.sellers.a@gmail.com | 18 |
| emma.murphy333@googlemail.com | 15 |
| megan.taylor0103@gmail.com | 15 |
| caro.danvers@gmail.com | 14 |
| lucy.russell333@googlemail.com | 14 |
| postmaster@completeitsystems.com.au | 13 |
| mailer-daemon@ln01.multimatics.com.au | 13 |
| amber.patel333@gmail.com | 13 |
| noa.meg.s@gmail.com | 10 |
| daisy.scott.a@gmail.com | 10 |
| rose.banks.a@gmail.com | 10 |
| amber.huber.s@gmail.com | 9 |
| moira.michaels@gmail.com | 9 |
| alexa.vernet.02@gmail.com | 9 |
| eli.borst@gmail.com | 7 |
| alexa.vernet.a@gmail.com | 7 |
| mailer-daemon@postoffice.telstra.net | 4 |
| hkjvufoef@completeitsystems.com.au | 4 |
| no-reply409@job.com | 3 |
| no-reply066@job.com | 2 |
| Total | 1150 |
With the exception of the two fake bounce messages sent from 68.233.235.190 on Fri Feb 11 20: 2:15 2011 and Fri Feb 4 04: 6:49 2011, it might be possible to claim that this was all above-board ... Because all of this traffic was sent to addresses on a "mailing list" ... To get off the list, all we had to do was send them a "removal request".
Certainly the email headers appear to be consistent, and genuine. However the number of From email addresses is a little suspicious ... Furthermore if you count all the subtle variations and permutations in the spelling and composition of the email address (not shown above) ... There were actually 50 different variations of the (full) From email address ... Which is more than just a little suspicious ... It's almost a smoking gun.
Later, following the trail to find out who was hosting this server, I discovered that it was hivelocity.net, who have an address registered in Tampa Florida ... Of course a Florida address does not necessarily make them spammers ... If we felt generous we could give them the benefit of the doubt ... Perhaps the account holder got a little over-enthusiastic with all this BUCE?
But the smoking gun is the two fake bounce notifications! It seems that spammers just can't resist the temptation to show off the well-honed and practised, but ill-gotten skills of their craft ... Having manufactured over a thousand emails finely-crafted to appear "genuine", they have yielded to temptation and included two with fake headers! There is now little doubt that 68.233.235.190 is being used by spammers. If hivelocity.net are legit and they value their reputation they should take a long hard look at this account.
Note: The Fake bounce notification technique is referred to as backscatter in the official postfix documentation.
Follow The Money!
A recent blog post by Larry Greenemeier in Scientific American concludes, not unsurprisingly, that the most effective way to prevent spam is to follow the money trail. If law-enforcement officials would simply track where the money goes and prosecute account-holders or freeze the accounts that were used to suck the money out of victims, it would do far more long-term damage to cyber-criminals then trying to shut-down their servers.
Cyber-criminals have spent a lot of time and effort adding sophisticated layers of complexity, obfuscation and security around servers, botnets and zombie master nodes. However their financial arrangements are often more transparent ... After all, they still want to get paid! By concentrating their efforts on the money trail, law-enforcement agencies can apply pressure where it has maximum effect ... To the financial lifelines leading to the scammers' wallets.
Of course this approach is not without its hazards. Despite rapid consolidation, many of today's cyber-scammers are still small time entrepreneurs taking their first teetering steps in a criminal career. So attempting to strangle their financial life-line may appear more like heavy-handed infringement of individual civil liberties by "officialdom". Nevertheless for the well-organised operations producing the new breed of malware, the approach of Following The Money may at least enable law-enforcement officials to identify who the bad guys are.
 PGTS Pty. Ltd. ACN: 007 008 568
PGTS Pty. Ltd. ACN: 007 008 568